Configuring encryption at rest
To enable encryption in MongoDB you should start mongod with --enableEncryption option.
Also, you need to decide where you are going to store the master key. You can store it either in external key manager which is the recommended way since this is necessary to meet HIPAA guidelines, or locally.
You will need to get an external key manager application that supports KMIP communication protocol. For example, this: https://www.townsendsecurity.com/products/centralized-encryption-key-management
To start mongodb with the new key use this command:
mongod --enableEncryption --kmipServerName <KMIP Server HostName> --kmipPort <KMIP server port> --kmipServerCAFile <ca file path> --kmipClientCertificateFile <certificate file path>
Now about the two last options:
--kmipServerCAFile <string>
Path to CA File. Used for validating secure client connection to KMIP server.
--kmipClientCertificateFile <string>
A string containing the path to the client certificate used for authenticating MongoDB to the KMIP server.
If the command succeeds then in the log file you will see the following messages:
[initandlisten] Created KMIP key with id: <UID>[initandlisten] Encryption key manager initialized using master key with id: <UID>
If a key already exists, then use the following command to start mongodb:
mongod --enableEncryption --kmipServerName <KMIP Server HostName> --kmipPort <KMIP server port> --kmipServerCAFile <ca file path> --kmipClientCertificateFile <certificate file path> --kmipKeyIdentifier <UID>
To read the full article about mongodb encryption at rest, follow this link: https://docs.mongodb.com/manual/core/security-encryption-at-rest/
Transport encryption
On server side
Before you can use SSL, you must have a .pem file containing a public key certificate and its associated private key.
MongoDB can use any valid SSL certificate issued by a certificate authority, or a self-signed certificate. If you use a self-signed certificate, although the communications channel will be encrypted, there will be no validation of server identity.
Set Up mongod with SSL Certificate and Key
To use SSL in your MongoDB deployment, start mongod including following run-time options:
- net.ssl.mode set to requireSSL. This setting restricts each server to use only SSL encrypted connections. You can also specify either the value allowSSL or preferSSL to set up the use of mixed SSL modes on a port.
- PEMKeyfile with the .pem file that contains the SSL certificate and key.
Syntax should be following:
mongod --sslMode requireSSL --sslPEMKeyFile <pem> <additional options>
You may also specify these options in the configuration file, as in the following example:
net:ssl:mode: requireSSLPEMKeyFile: /etc/ssl/mongodb.pemSet Up mongod with Certificate Validation
Along with options from the previous methods you should also set up CAFile with the name of the .pem file that contains the root certificate chain from the Certificate Authority.
Syntax:
mongod --sslMode requireSSL --sslPEMKeyFile <pem> --sslCAFile <ca> <additional options>
If you prefer using a configuration file, then:
net:ssl:mode: requireSSLPEMKeyFile: /etc/ssl/mongodb.pemCAFile: /etc/ssl/ca.pemDisallow Protocols
To prevent MongoDB servers from accepting incoming connections that use specific protocols, including the --sslDisabledProtocols option, or if using the configuration file the net.ssl.disabledProtocols setting.
mongod --sslMode requireSSL --sslDisabledProtocols TLS1_0,TLS1_1 --sslPEMKeyFile /etc/ssl/mongodb.pem --sslCAFile /etc/ssl/ca.pem <additional options>
If you use config file:
net:ssl:mode: requireSSLPEMKeyFile: /etc/ssl/mongodb.pemCAFile: /etc/ssl/ca.pemdisabledProtocols: TLS1_0,TLS1_1SSL Certificate Passphrase
The PEM files for PEMKeyfile and ClusterFile may be encrypted. With encrypted PEM files, you must specify the passphrase at startup with a command-line or a configuration file option or enter the passphrase when prompted. To specify the passphrase in clear text on the command line or in a configuration file, use the PEMKeyPassword and/or the ClusterPassword option.
On client side
For C#:
To read a full article about mongodb transport encryption, follow this link: https://docs.mongodb.com/manual/core/security-transport-encryption/
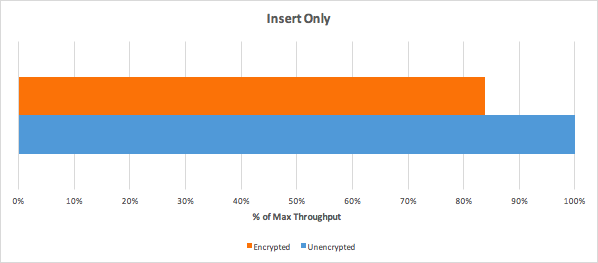
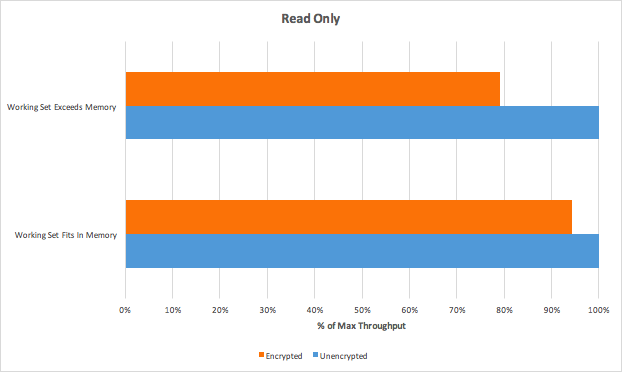
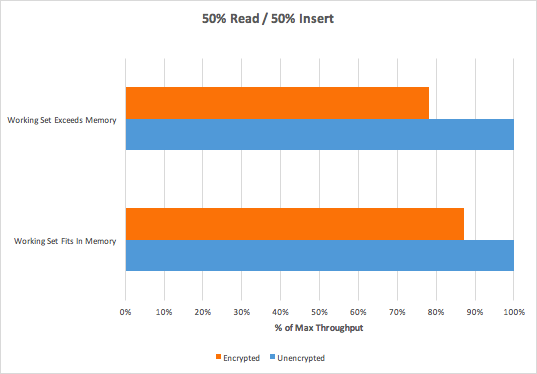
Performance (of encryption at rest)
CPU: 3.06GHz Intel Xeon Westmere(X5675-Hexcore)
RAM: 6x16GB Kingston 16GB DDR3 2Rx4
OS: Ubuntu 14.04-64
Network Card: SuperMicro AOC-STGN-i2S
Motherboard: SuperMicro X8DTN+_R2
Document Size: 1KB
Workload: YCSB
Version: MongoDB 3.2
In such environment they've got following results:
In addition to throughput, latency is also a critical component of encryption overhead. From our benchmark, average latency overheads ranged between 6% to 30%. Though average latency overhead was slightly higher than throughput overhead, latencies were still very low—all under 1ms.
Average Latency (µs)
|
Unencrypted
|
Encrypted
|
% Overhead
| |
|---|---|---|---|---|
| Insert Only | Average Latency | 32.4 | 40.9 | -26.5% |
| Read Only |
Working Set Fits In
Memory Avg Latency
| 230.5 | 245.0 | -6.3% |
| Read Only |
Working Set Exceeds
Memory Avg Latency
| 447.0 | 565.8 | -26.6% |
| 50% Insert / 50% Read |
Working Set Fits In
Memory Avg Latency
| 276.1 | 317.4 | -15.0% |
| 50% Insert / 50% Read |
Working Set Exceeds
Memory Avg Latency
| 722.3 | 936.5 | -29.7 |
To read the full article, follow this link: https://www.mongodb.com/blog/post/at-rest-encryption-in-mongodb-3-2-features-and-performance